Our other sites:
Data centres are a vital component in modern life’s reliance on the safe movement and storage of information. As well as digital breaches, these sites are also vulnerable to physical break-ins, with fences and gates providing the first line of defence against unauthorised access to servers, power generators, and other critical assets.
When protecting your data centre, we recommend addressing the following five security layers to ensure total protection at every level. This strategy should be used in tandem with the five Ds of perimeter security: Deter, Detect, Deny, Delay, Defend.

1. Protect the Outer Perimeter
Defending your data centre against unauthorised entry is the first step in preventing physical security breaches.
Fencing
Select a product that is tested and certified to a forced entry standard such as LPS 1175, and that withstands forced entry attempts using different tool categories. Also make sure the design fits with your security and privacy needs, as well as blending with the facility’s surroundings.
Fence spikes and security toppings such as barbed wire, spikes and rotary systems can further enhance the levels of security against intrusion, damage, acts of vandalism or terrorism but check planning restrictions in the area and be mindful of their use in residential settings. Areas with restrictions are where fencing design comes into play. To protect a data centre from the specified risks while adhering to local regulations, our Barbican Defender Xtreme A1 was installed. With cranked pales it projects a strong image with anti-climb properties, but does not create a hostile environment and fits better with the surrounding environment than barbed wire and mesh fencing.
Gates and access control
A perimeter security system should be completed with the appropriate type of gate, whether it be swinging, sliding or bi-folding. A proper gate ensures no weak points exist around the boundary, and serves as secure a checkpoint to let authorised traffic pass in and out. Combine gates with the likes of traffic arm barriers or road blockers to slow vehicles, and be sure to include pedestrian gates for safe access for staff and clients.
Hostile Vehicle Mitigation
With the rising threat of vehicle-borne attacks, Hostile Vehicle Mitigation (HVM) measures are an increasingly important aspect of any physical security strategy. Add another line of defence with unobtrusive HVM solutions such as certified crash rated bollards, barriers and road blockers. Additionally, another line of standoff fencing can be installed around the main perimeter fence. Linebacker PNR, with its natural post and rail appearance, provides an unobtrusive fence which is capable of stopping a 7.5 tonne vehicle travelling at 50mph.
CCTV and PIDS
CCTV cameras enable 24/7 monitoring of your facilities against potential threats. When paired with CCTV and intruder alarm systems such as PIDS which can be mounted on any stable fencing in good condition, and offer highly efficient and discreet threat detection.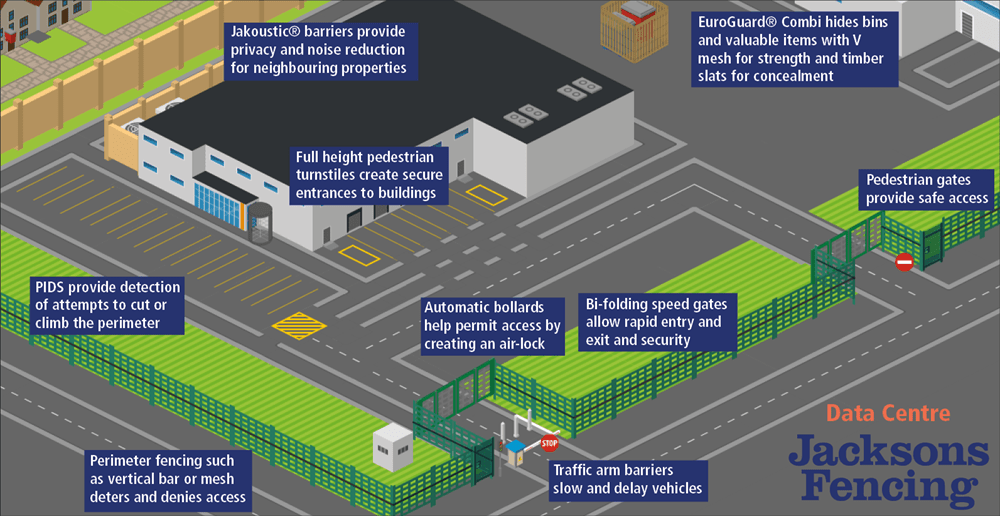
2. Protect Assets Within the Perimeter
Data centres feature specialised and costly equipment such as power generators and air conditioning units, and also house staff vehicles and offices. Some considerations in monitoring and controlling movement within the zone:
CCTV
Infrared or thermal detectors track movement, and combined with audio warnings issued by the CCTV operator are an efficient way to de-escalate threats.
Security Lighting
Installing security lighting systems ensures that intruders are easily detected at night. If your facility resides in an area that enforces light pollution restrictions, event-triggered lighting solutions or CCTV systems with thermal imagery capabilities could be the answer.
Noise Control
Consider controlling the noise of power generators and a/c units to keep neighbours happy by enclosing them in special sound-dampening structures like timber acoustic barriers.
3. Protect the Server Building
The third layer in data centre protection is securing the server room itself.
Fire and Intruder Alarms
These systems are vital in keeping your server buildings safe, and can link to CCTV monitoring for an extra level of security.
Key Access Point Control
Protect entry points to deny access to unauthorised personnel with turnstiles and keypad entry systems.
4. Protect the Server Rooms
Once the server rooms are breached, the data is at high risk. Some measures to consider in defending your server rooms:
CCTV
Monitor the server floor with multidirectional cameras.
Audio Deterrents
Install speakers from which to issue warnings or announce to security staff that a breach has occurred.
Internal Gates and Compounds
Secure gates installed in corridors, and mesh compounds around server units are ideal for protecting critical units from sabotage.
5. Protect the Data Itself
Your final line of defence in your data centre is protecting the data racks themselves. Here are some controls to consider:
Monitor Cabinet Doors
Install camera systems within the racks to track the opening of cabinet doors.
Utilise Smart Technology
Employ smart tech to enable integration and communication across all of your security layers – from the perimeter fencing to server room checkpoints – to easily grant or deny access throughout your data centre facilities.
Security points to consider
Jacksons Fencing Solutions for Data Security Centres
Jacksons Fencing offers a wide range of security fencing for data centres. Our fencing is available in a variety of heights and styles that blend into any surroundings, and we offer toppings such as spikes, gates, hostile vehicle mitigation products and perimeter intrusion detection systems (PIDS) that can easily be combined with closed-circuit television (CCTV) for an integrated security solution.
There are many considerations when choosing a perimeter fencing solution to keep your data centre safe and secure from unauthorised access. Jacksons Fencing offers you a range of robust, customisable solutions accompanied by our 25-year guarantee.
Contact us today and one of our experts will help you find the right solution for your project.
Related Content
Read about perimeter fencing in layered data centre security models:
Related Products
Jacksons Fencing have a large range of related products, all complete with our 25 year guarantee. If you cannot find the item you are looking for, please do not hesitate to call our friendly sales team.
Related Content
Top